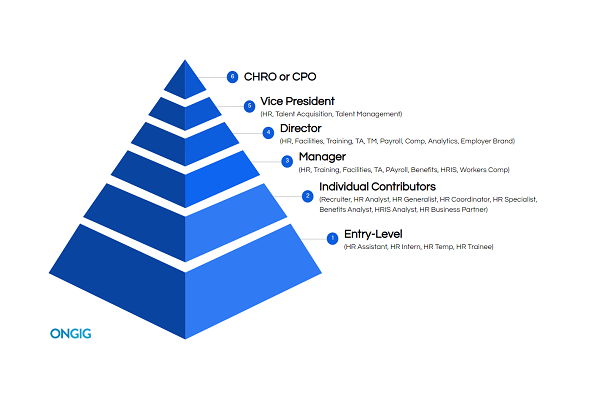
Hire The Best Cisco Engineers In May 2021
has been created for anybody who needs to study ethical hacking from scratch. Besides introducing you to theoretical ideas of networking, web purposes, and coding, you’ll get hands-on apply by detecting vulnerabilities in an e-commerce website. A foundational information of networking is a must as everything in the digital world relies on that. Networking helps you find out how computers interact with each other and how data will get transferred.
Personally I skilled Good bcz whenever I had missed any of the courses they helped me to rewinding the recorded videos, and most of the time respected mentors solved my queries. Thanks to verzeo for offering an area platform for internship students. Tracking the sources of hacking and being aware of the kinds of assaults are as important as taking safety measures.
Is A Career In Cybersecurity A Great Fit For You?
So, hopefully, you gained’t be compelled to study out-of-date expertise that nobody makes use of right now. Every even semester, the seniors arrange extra lessons on Algorithms, Discrete Math, and Data Structures . GAWDS is a society filled with tremendous gifted people who are experts in their fields and with whom you presumably can be taught and grow as a developer.
Cyber security has been evolving as a enterprise for many years due to the increasing price of cyber crimes. Any trade that trades on-line or has delicate knowledge needs a cyber security skilled to protect its date from such criminals. Cyberspace is a popular network that could be accessed by anybody from every nook of the globe. This course to study cyber security online helps understudies to learn in regards to the primary ideas of cybersecurity and moral hacking.
Fortinet Network Security
At the same time, as the risk panorama expands, there’s a stronger need for CISOs to recognise vulnerabilities within the context of business danger and utilise information to prioritise cybersecurity efforts. This innovative method will support Indian organisations’ concentrate on the vulnerabilities that weigh the most and mitigate true business risk, instead of focusing on flaws that have the lowest chance of being exploited. A safety analyst is answerable for detecting and preventing cyber threats for a corporation.

One key problem going through firms is the necessity to undertake the correct method to cybersecurity issues. Traditionally, the steps they take on this regard are reactive, somewhat than proactive. Companies ought to assess their important business activities holistically and implement pre-planned cybersecurity measures, as an alternative of ready for a cyber-incident and thereafter endeavouring to detect and patch vulnerabilities. This takes up appreciable time, expense and experience, which ought to be given appropriate allocation in insurance policies and budgets.
Msc In Cyber Security In Eire
Candidates must seem personally with the necessary documents earlier than the counseling committee on the scheduled date and time. To be eligible for BTech Cyber Security, applicants must full their 10+2 from a recognized board or university with Maths, Physics, and Chemistry as compulsory topics and secure a minimal mixture score of 50%. Institute helped me in all means from getting expertise till placement assistance. At SevenMentor you will be dealing with ongoing Cyber Security actions and bit by bit assignments which have a excessive significance in the corporate world, and the academic program is planned by industry specialists.
Data Security is the process of offering security to the data which is current in any system software or any platform. This consists of security to all kinds of data shops similar to databases, warehouses, purposes, etc. The knowledge security is delicate to all forms of malicious content such as worms, trojans, viruses, and so forth.
Cyber Safety Salary In Eire
CXOtoday has a well-networked and robust community that encourages discussions on what’s taking place on the planet of IT and its impact on businesses. The candidate is required to carry out and assist within the conduct of Code Security Review assessments for crucial banking functions. They will carry out false-positive-analysis and evaluation findings from the automated assessment. The candidate ought to know mobile software security assessment and expertise in API and Thick client purposes safety evaluation.
So you’ll be liable for investigating cybercrimes like scams, trafficking, terrorist actions, and so on. They examine the security practices and protocols and check for any vulnerabilities in the client’s system, software program, utility, or network. This assessment is then documented and the findings are mentioned with the stakeholders. They may be liable for educating the corporate employees about best safety practices. Strengthen your cloud safety structure and improve your readiness to absorb new cloud services.
Top Recruiting Companies For System Safety Analyst
For admissions in Gujarat you want to clear the GUJCET entrance examination, the higher the rating the greater the list of eligible faculties, it’s similar to the JEE mains that we usually write for engineering programs. After making use of for the faculty a merit record was released and I was referred to as for counselling, I chose CSE as my division. I suppose so nmims college mumbai and mukesh patel faculty has the best infrastructure in mumbai.the school seems just like the 5-star resort. lecture rooms are fairly giant and good.They are very neat and tidy. Our all school rooms and labs are equiped with air conditioners.
Auditors are answerable for producing a security report primarily based on their evaluation, which additional helps the organization formulating strategies to protect priceless belongings from adversaries. It’s potential that the company is hiring extra cyber professionals to proceed bolstering that work in these areas and defending person knowledge. Information security analysts should educate users, explaining to them the significance of cybersecurity, and tips on how to defend their data. They have to speak this data in a clear and fascinating method. Therefore, data security analysts want robust oral and written communication abilities. A system security analyst safeguards the info and knowledge methods of an organisation.
Classes To Learn From Air India Information Breach
As Regional Director of India, the Middle East and Africa , Mr. Agarwal, is responsible for main the EC Council’s business operations in data safety, coaching, and certifications for enterprise acceleration. He is also liable for managing all the direct companies for EC-Council, globally. As companies struggled to create work-from-home set-ups for employees, the one aspect that was uncared for by most was cybersecurity. With employees logging in from units outdoors the perimeter of their company’s cybersecurity web, methods have turn into weak. The bottomline is info safety becomes part of the business when it’s considered simultaneously with the digital path the company has visualised.
Cyber safety career professionals are tasked with the responsibility to guard organizations and generously paid to take action. If you’ve been serious about pursuing a cybersecurity career, hopefully our post gave you sufficient information to make a key determination moving ahead. There is not any secret answer to this but we believe that having an understanding of your interests, hobbies, and personal values is necessary to creating positive they align with your cyber safety profession targets. Successful cybersecurity analysts are curious, inquisitive, and learning every day. Good Pay – In India, cyber safety career heads of companies can attract packages as excessive as INR 2 crores to 4 crores.
Institute Of Know-how
As partaking as the subject sounds, studying about Cyber Security necessitates an excellent understanding of the various networks obtainable in the tech world. This also implies that professionals working underneath this area need to continuously keep themselves up to date with the latest developments and developments to offer secure methods to their clients. Defining a successful Cybersecurity system means the system has multiple layers of safety that’s spread across all nodes, networks, data and packages that an individual or a corporation aims to keep protected. Information Security Strategic Solutions is fashioned by Subramaniam Sankaran, who has a rich industry experience in Information Security area and a really well-known skilled. This program facilitates bi-weekly mentoring periods with extremely skilled mentors. The advantages of this program embrace profession help packages, providing entry to curated jobs, organizing placement drives, profession mentorship programs, interview preparation workshops, and extra.
So professional relationship helps not only to find a good job, but additionally to get profession advice in your future. So use social community channels to find groups related to your jobs and join these teams. GCIH exhibits you could handle security incidents by understanding frequent assault strategies, vectors and instruments as well as defending towards and/or responding to such assaults once they occur.
Companies
A rise in the menace of cyber assaults has increased the demand of cybersecurity professionals. Also meet Bytebandits, the staff from India which secured the eighth position in CSAW CTF 2020. As demand for cyber security professionals in the UK and worldwide continues to surge, this course will put together you for the problem of maintaining IT environments safe and safe in a world the place data is continually beneath attack.
GSEC shows that you’re capable of to deal with IT techniques palms on roles related to security duties. Intermediate and expert-level certifications presume that you have in depth job experience and an in depth grasp of the topic matter. Cyber security certifications administered by the impartial accrediting organizations. These individuals work with regulation enforcement agencies to compile proof for authorized circumstances, draft technical reports or offer expert testament in trial, and prepare law enforcement in laptop evidence ways. As per the organisation wants he suggests one of the best solution to secure companies’ data.
Cyber
Chief Information Security Officers in the cyber safety career area oversee the security capabilities inside the group. Dr. Rajendra Kumar is a senior officer within the Indian Administrative Service (I.A.S.). In his current capacity, he’s main the policy formulation and implementation of varied schemes underneath the Digital India, e-governance, electronics manufacturing, knowledge safety and cyber security domains within the nation. The perform of a security operations group and, incessantly, of a safety operations center , is to monitor, detect, examine, and respond to cyberthreats across the clock.
Finally, Chartered Accountants are usually leaders within the control course of that ensures risks are mitigated and have a well-deserved reputation for always worrying with safety for his or her shoppers and employers. Chartered Accountants, then, are well-placed to step into the function of proactively guarding the interests of their shoppers and organisations in an period when fast technological change is creating ever greater risk. Though they don’t appear to be IT-focused, Chartered Accountants can comprehend fundamental cybersecurity information that permits them to contribute towards their organisation’s defences. This is an important talent when threats come from so many different instructions and organisations can not at all times afford to defend each entrance directly.
Career In Cyber Security
In today, firms and banks are utilizing computers to retailer and process the information. Cyber criminals are attacking these networks to steal delicate data of the organization. We don’t charge any quantity from our students for counseling or a number of different services that we offer; for any support from the visa utility, contact us.
In this module, you’ll study what assault vectors are and how they are often utilized to extract and destabilize a system by concentrating on specific vulnerabilities. These embody Trojans, Viruses, Worms, and far more malware that pose a threat to networks and other methods. Cryptography is the follow and the research of strategies for securing data from unauthorized entry and utilization. Web security refers again to the instruments and strategies employed to protect a net site or an online utility from cyber assaults. It involves detecting, preventing, and responding to the various cyber-attacks and regulating web site safety.
Networking
Cisco Tetration provides holistic workload safety with utility visibility and segmentation. Get more protection in opposition to phishing, ransomware, business email compromise, and extra. In addition, Cisco Cloud Email Security blocks and remediates e-mail threats, and Stealthwatch Cloud displays your IaaS situations and alerts on suspicious activities. Cisco Cloud Security products ship a broad, efficient security resolution on your multicloud world. Securing the general public cloud is an increasingly tough problem for companies.
Bad hackers use their information of laptop systems for unhealthy purposes, moral hackers plug the vulnerabilities. Every huge firm wants moral hackers to protect itself from cyber-attacks. Every function in IT should assume from a security angle to whatever they buy, do and implement. As far as budding security professionals are concerned, developing a deep technical domain experience is a must.
Practices To Contemplate Whereas Implementing A Zero Trust Security Mannequin
As Telecom Secretary, he was liable for driving a quantity of key policies and techniques masking licensing, spectrum management, National Broadband Plan, Convergence, Manufacturing, Investment, safety, R&D and the National Telecom Policy 2012. He was the principal architect behind a triad of insurance policies overlaying Telecommunications, Electronics and Information Technology that was unveiled in draft form by the Government of India in October, 2011. The thrust of these insurance policies is to optimally leverage Information and Communication Technologies to find revolutionary solutions in education, well being care, financial inclusion, e-governance, skill development, employment generation, and so forth.

The issues confronted by data safety professionals are sometimes left unanswered under this legislation, and companies are pressured to depend on inner or cross-border finest practices to organize themselves to pre-empt cyber threats. The advent of recent technologies similar to artificial intelligence, 5G, the Internet of Things and cloud computing have intensified this inadequacy. Cybersecurity Foundation Certification is designed with the vast knowledge of the global perspective of challenges that one faces while mapping a secure system while overlaying the most important cyber roles needed to offer a solid system. With all the hacking and information manipulation, cybersecurity has turn into a necessity of the hour now. By going via this certification, you will find out about threat developments which may be most alarming across the web presently as properly as their impression on cybersecurity. This is likely considered one of the programs on cyber safety that mainly focuses on the subject of the Internet of Things .
Iso 27001 Certification And Its Upkeep
Interact with globally renowned security researchers, hear them share their expertise and experience. Shipra comes with over 15 years of experience in monitoring enterprise technology market and the CIO area. She has the ability to provide very high-impact content in the enterprise expertise space in addition to on the dynamics shaping the CIO landscape.
IT professionals with minimal 5 years experience can apply for CISA. It involves identifying and plugging vulnerabilities and different flaws in an enterprise surroundings. Free and short on-line programs from American instructional institutes are available. These free programs principally function teasers to entice college students and professionals to enroll for bigger packages.

